Burp Web Academy 访问控制漏洞
0x01. PortSwigger Web Security Academy
PortSwigger Web Security Academy 是 Burp Suite 官方推出的免费 Web 安全学习靶场,在学习 Web 安全知识的同时,还可以练习 Burp Suite 的实战技能。
本篇文章讲解 Web Security Academy 之中的访问控制漏洞(Access Control Vulnerabilities)章节。
- Part1: Burp Web Academy 访问控制漏洞
- Part2: Burp Web Academy 访问控制漏洞(二)
- Part3: Burp Web Academy 访问控制漏洞(三)
0x02. 访问控制漏洞
2.1 Lab: Unprotected admin functionality
This lab has an unprotected admin panel.
Solve the lab by deleting the user
carlos.
试了几个目录都是 404:
- /admin
- /administrator
- /panel
- /system
- /manage
- /users
查看题目答案,是通过 /robots.txt 找到对应的地址:
1 | User-agent: * |
2.2 Lab: Unprotected admin functionality with unpredictable URL
This lab has an unprotected admin panel. It’s located at an unpredictable location, but the location is disclosed somewhere in the application.
Solve the lab by accessing the admin panel, and using it to delete the user
carlos.
先查看页面源码,发现如下 JavaScript 代码:
1 | var isAdmin = false; |
2.3 Lab: User role controlled by request parameter
This lab has an admin panel at
/admin, which identifies administrators using a forgeable cookie.Solve the lab by accessing the admin panel and using it to delete the user
carlos.You can log in to your own account using the following credentials:
wiener:peter
登陆后,发现 HTTP 请求头中存在 Cookie: Admin=false; session=0hwkQVOKLVVfEcCSKM2rNEIEHbJ0aU24,可以使用 Burp 的请求头修改更能,把 Admin 设置为 true,参考:Burp Web Academy 信息泄露。
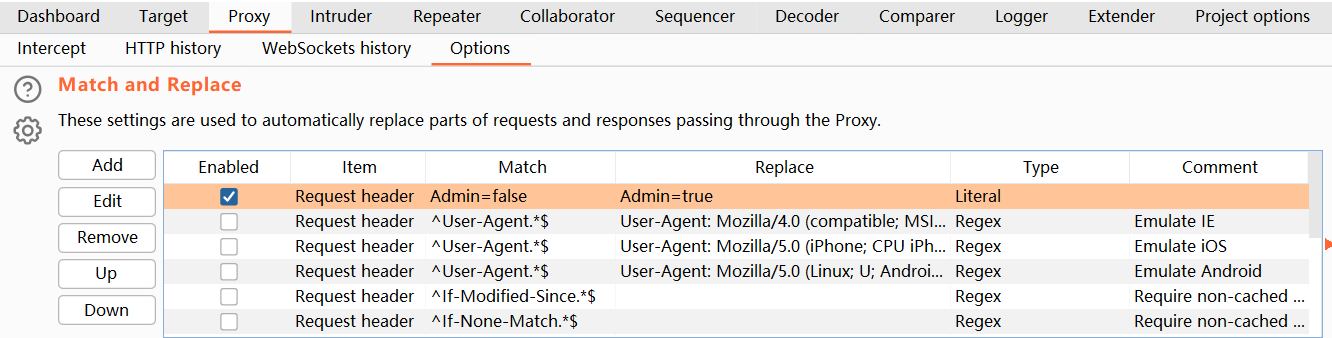
之后,就能看到 Admin panel 了,可以删除指定用户。
2.4 Lab: User role can be modified in user profile
This lab has an admin panel at
/admin. It’s only accessible to logged-in users with aroleidof 2.Solve the lab by accessing the admin panel and using it to delete the user
carlos.You can log in to your own account using the following credentials:
wiener:peter
找了一圈没啥线索,尝试修改 Email,发送的 HTTP POST 请求包:
1 | POST /my-account/change-email |
HTTP 响应包:
1 | 302 Found |
所以,看起来可以尝试在修改 Email 的 JSON 中指定 roleid=2:
1 | {"email":"2@gmail.com", "roleid":2} |
2.5 Lab: User ID controlled by request parameter
This lab has a horizontal privilege escalation vulnerability on the user account page.
To solve the lab, obtain the API key for the user
carlosand submit it as the solution.You can log in to your own account using the following credentials:
wiener:peter
横向越权问题:
登录后重定向到
/my-account?id=wiener直接修改
id参数:/my-account?id=carlos
2.6 Lab: User ID controlled by request parameter, with unpredictable user IDs
This lab has a horizontal privilege escalation vulnerability on the user account page, but identifies users with GUIDs.
To solve the lab, find the GUID for
carlos, then submit his API key as the solution.You can log in to your own account using the following credentials:
wiener:peter
依然是横向越权:不过这次不是简单的把用户名作为 id,而是使用了 GUID。
首页看到很多文章,一个一个点进去,找到 carlos 发表的文章,然后使用他的 GUID 来做横向越权即可。
2.7 Lab: User ID controlled by request parameter with data leakage in redirect
This lab contains an access control vulnerability where sensitive information is leaked in the body of a redirect response.
To solve the lab, obtain the API key for the user
carlosand submit it as the solution.You can log in to your own account using the following credentials:
wiener:peter
登录后,直接访问 /my-account?id=carlos 尝试水平越权,此页面会做 302 跳转,然而页面里面已经写明了 carlos 的 API Key。
2.8 Lab: User ID controlled by request parameter with password disclosure
This lab has user account page that contains the current user’s existing password, prefilled in a masked input.
To solve the lab, retrieve the administrator’s password, then use it to delete the user
carlos.You can log in to your own account using the following credentials:
wiener:peter
还是水平越权问题,直接修改 URL 为 /my-account?id=administrator,就可以看到密码字段,之后查看网页源码即可:
1 | <input required type=password name=password value='m44eumksx4bu1z8a9pq3'/> |
2.9 Lab: Insecure direct object references
This lab stores user chat logs directly on the server’s file system, and retrieves them using static URLs.
Solve the lab by finding the password for the user
carlos, and logging into their account.
点击 View transcript,会触发对话文件下载,PATH 是 /download-transcript/2.txt,直接改成 /download-transcript/1.txt 得到密码。
1 | 200 OK |
0x03. 小结
- URL 探测
- 使用专用的扫描器,探测管理地址
- 查看
/robots.txt文件 - 下载其他用户的关联文件
- 源码查看
- 是否存在关键的 JavaScript 代码
- 是否存在注释内容
- 密码掩码保护查看原始内容
- 参数修改
- 替换 URL 中的关键参数,实现水平越权
- 替换 Cookie 中的参数,实现越权
- 使用 Burp 修改 HTTP 请求头,支持正则匹配,可以修改任意行,包括使用内置的
User-Agent模拟手机
- 使用 Burp 修改 HTTP 请求头,支持正则匹配,可以修改任意行,包括使用内置的
- 替换或修改 POST 请求中的参数,实现关键信息变更
- 尝试参数替换越权时,如果发生跳转,需要关注
301、302等跳转页面的信息